Get Active Directory Security at 80% in 20% of the time
Get Active Directory Security at 80% in 20% of the time
Active Directory is quickly becoming a critical failure point in any large-sized company, as it is both complex and costly to secure..
People and process
PingCastle was born based on a finding: security based only on technology does not work. That’s why the company focuses on process and people rather than just technology. We do not sell products !
Download our tool and apply our methodology or check how our partners can bring more value to you.
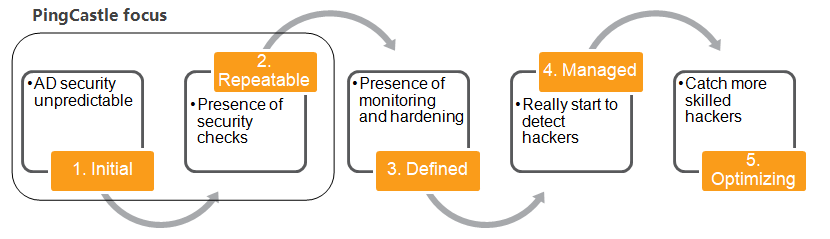
A methodology based on maturity
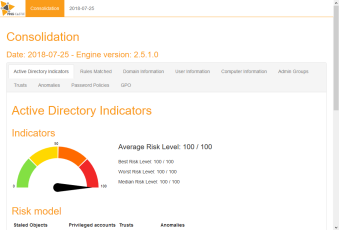
We do not provide solutions to protect your infrastructure. Instead, we provide tools to discover what you have to protect, evaluate its security level and provide insights on whether the allocated budget has been effectively utilized.
For IT Operations
Help detect critical security issues, get an overview of the technical situation and provide guidance and advices to fix the issues.
For IT Management
Evaluate the current security level, indicates the presence of critical risks and advice on priorities for the action plan.
Maturity and Results
Establish a common vocabulary between IT Management and IT Operations and provide a maturity evaluation
Deliverables
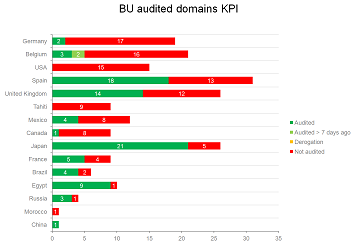
We focus on deliverables you need. What is your criticality level? Do you know how many domains do you have ? Can you produce a dashboard for management ? Checkout our documentation
“For CISO, by CISO”
-Engie, a French multinational, led a 2-year Active Directory security program and had more than 300 domains. PingCastle is the result of this program. PingCastle’s objective is not to reach a perfect security but to jump start a change.

Vincent LE TOUX
CTO
With 15 years experience as an IT and 5 years on the group CISO team, Vincent LE TOUX is an experienced security consultant whose specialty is the interconnection of process and technology.
He has also made many open source contributions such as mimikatz, OpenPGP, OpenSC, GIDS applet, etc. Finally, he has presentated at security events, mainly FIRST, BlueHat, Troopers, Hack In Paris, Blackhat Europe and BlackHat US .