Delegation
Check for problem in delegation modelHome » Documentation »
When delegating the right to create users or computers mistakes can be made which open the path to an attacker. PingCastle can scan quickly the permissions to find such vulnerability.
Prerequisites
AD connectivity
Access to the Active Directory via a local account or an account from a trusted domain
No local requirements
PingCastle requires only the dotnet framework version 2 available starting from Windows 2000
No domain requirements
Any users can query the objects stored in the domain or the GPO objects.
Build it
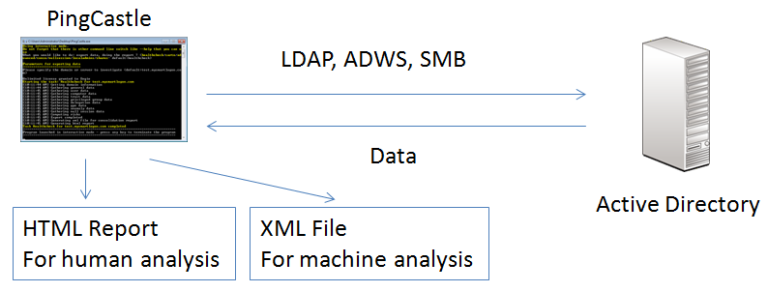
The report can be generated in the interactive mode by choosing “healthcheck” or just by pressing Enter. Indeed it is the default analysis mode.
It can be run using the command:
PingCastle.exe --healthcheck --server mydomain.com
Description
The report is divided in 2 parts. The parts are described below.
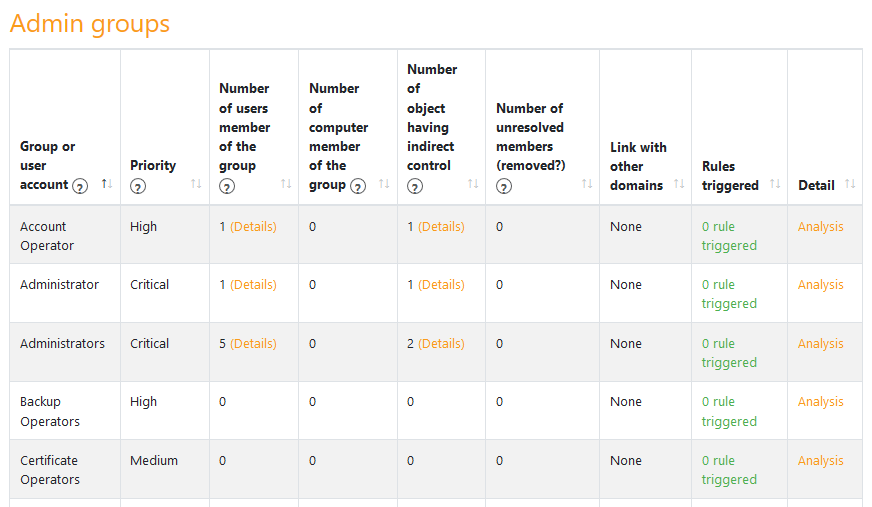
This section indicates the main findings and the associated graph can be shown when clicking on the group or user account.
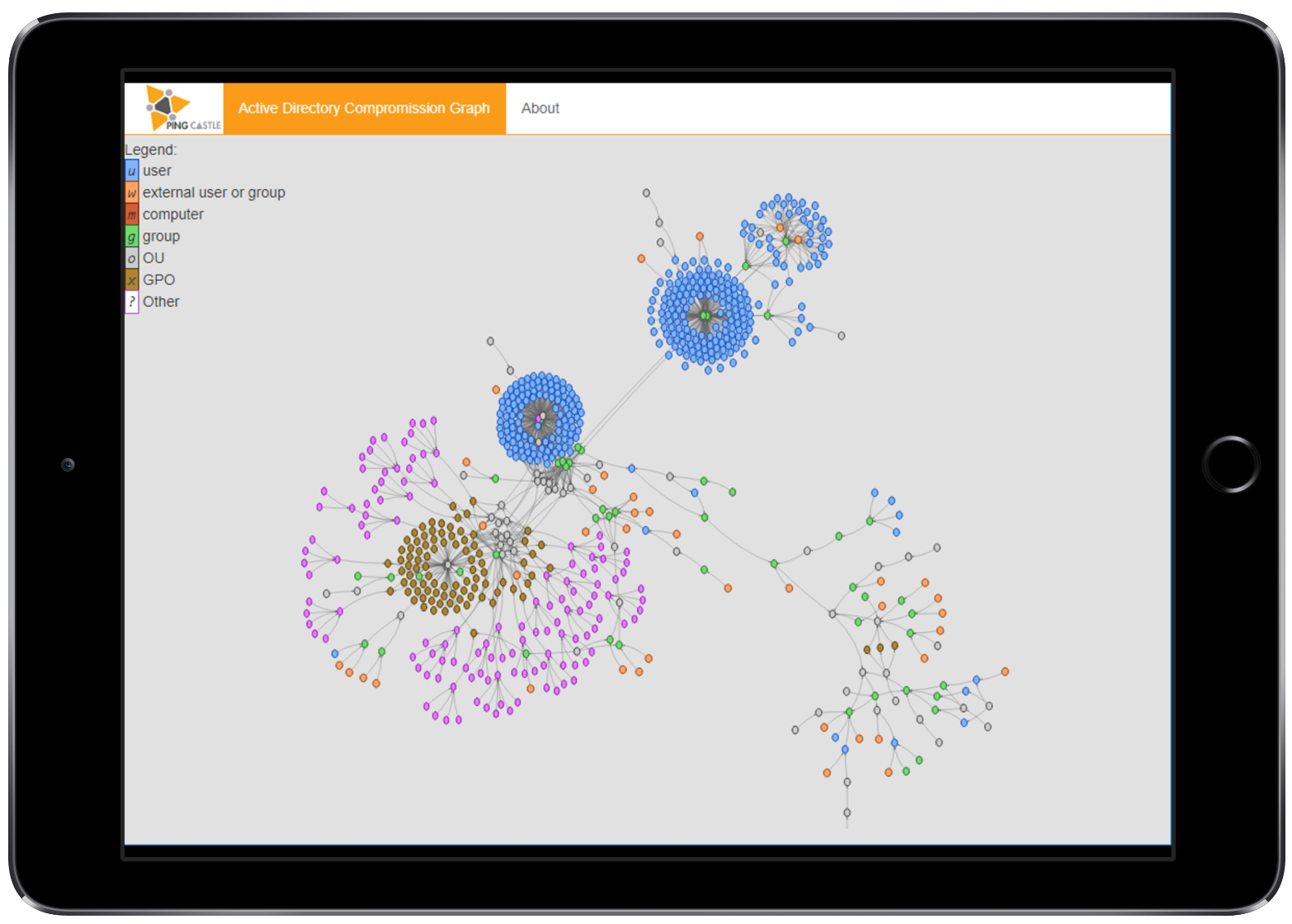
A click on detail display the compromission graph
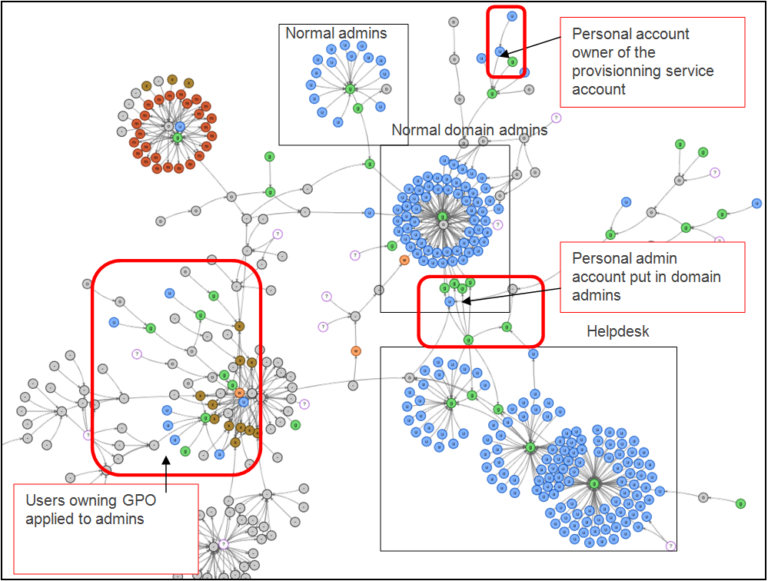
The relation between the group or user account to monitor and the objects which can take control of it are drawn.
The read it, you have to find the root object by following the arrow object by object until you find it.
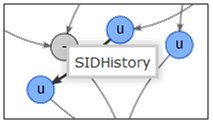
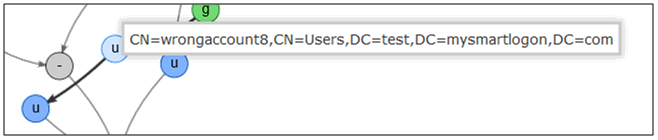
Then you have to identify the other account and understand why they are linked. The best way is to stand the mouse on a link until a notice is displayed. This notice indicates why the node has been attached.
A real life example: