Documentation
This is how you can get things done.How to produce PingCastle reports
Click on an icon to see how reports can be generated. The following page describe the requirements, the process. Examples can be downloaded.
How to use PingCastle
Install
Follow the steps to install PingCastle on a system.
Run PingCastle
See how to run the program in interactive or command line mode
Quick start
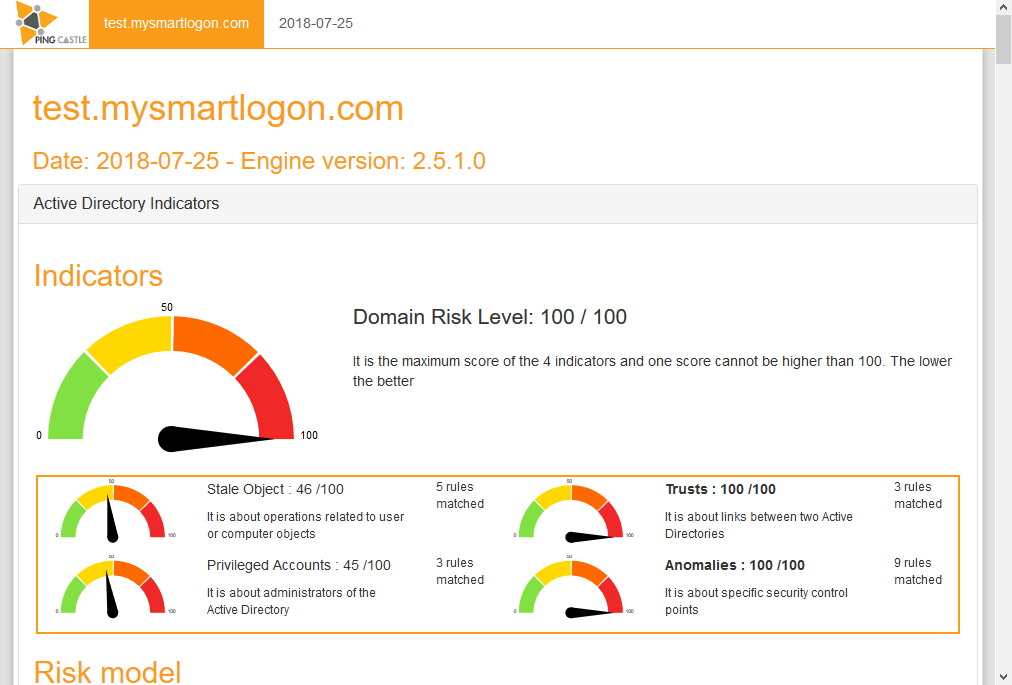
Health Check
This is the default report produced by PingCastle. It quickly collects the most important information of the Active Directory and establish an overview. Based on a model and rules, it evaluates the score of the sub-processes of the Active Directory. Then it reports the risks.
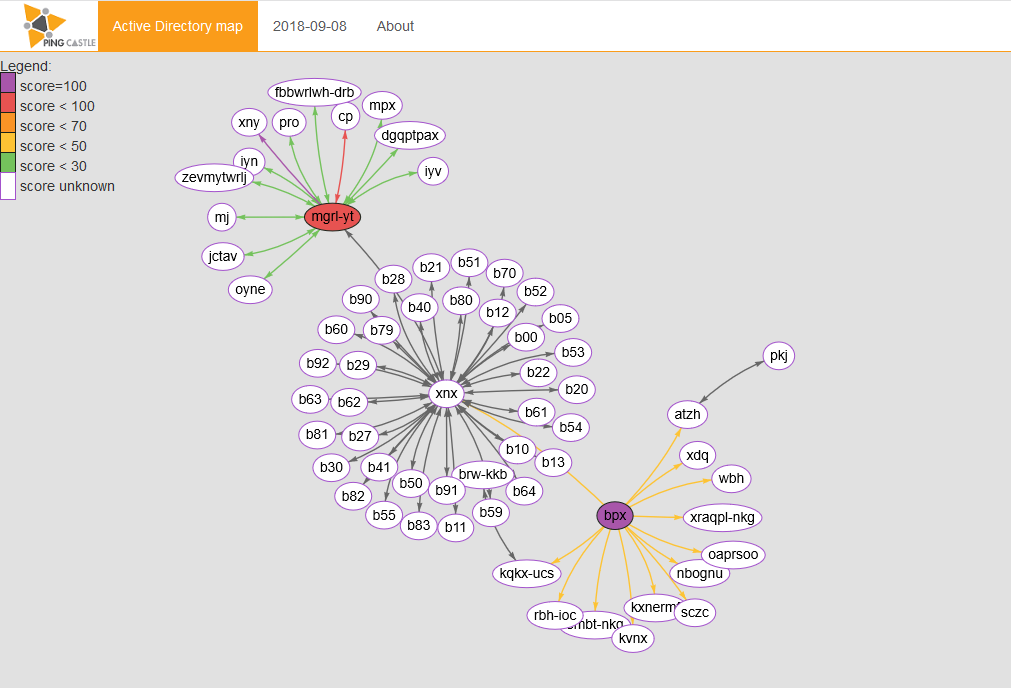
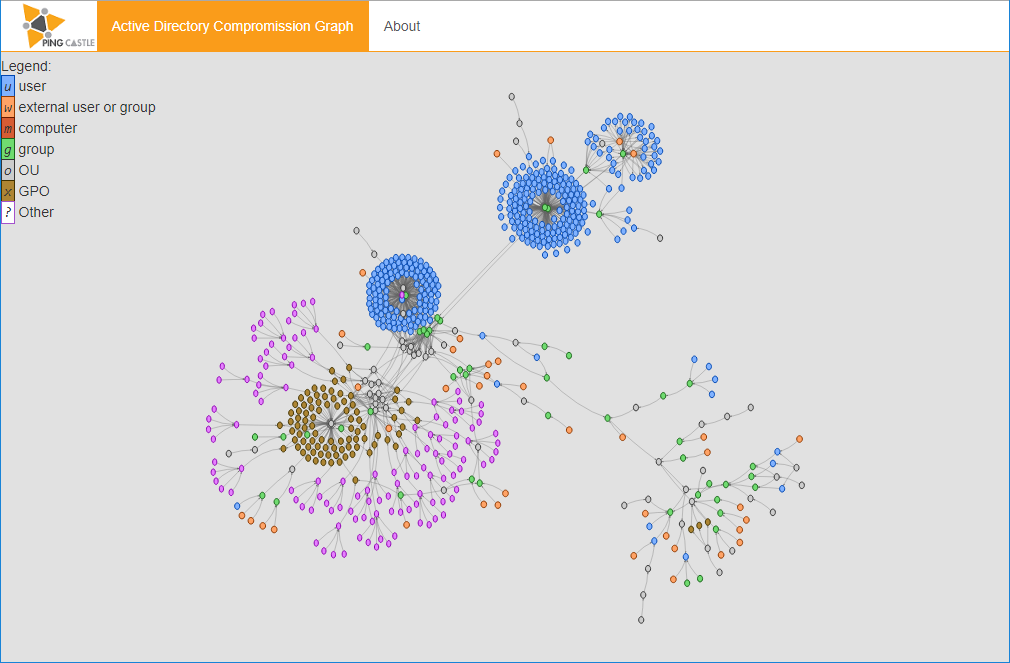
Active Directory map
This report produces a map of all Active Directory that PingCastle knows about. This map is built based on existing health check reports or when none is available, via a special mode that collects the required information as fast as possible.
Without business context input
Deploy and collect reports
Monitoring domains from a bastion can be easy. But for those without network connection it might be difficult. There are many deployment strategies available with PingCastle.
Consolidation
For complex environments and with business context input
Managing
Dashboard
When contextual information is available, PingCastle can produce a dashboard to facilitate the representation of the collected data. The view is both at a global and at a local level.
Scanning the environment
Delegation vulnerability
When delegating the right to create users or computers, mistakes can be made which opens the path to attackers. PingCastle can scan quickly the permissions to find such vulnerability.
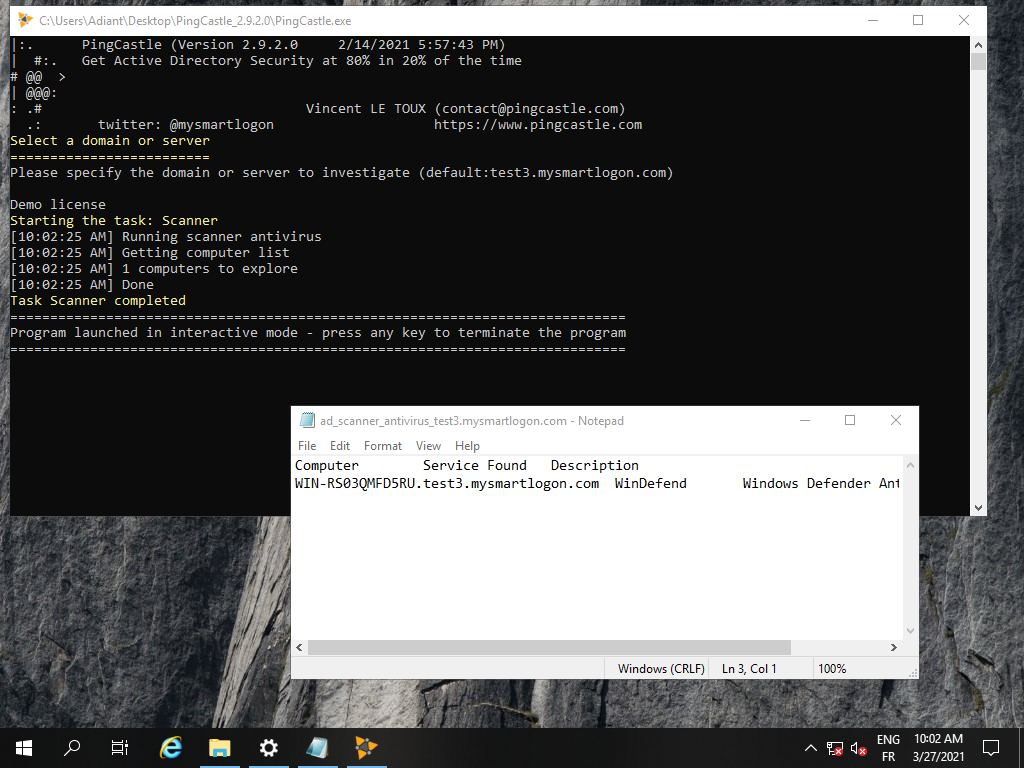
Scanner & Export
Checking workstations for local admin privileges, open shares, startup time is usually complex and requires an admin. PingCastle’s scanner bypass these classic limits. You can use also PingCastle to dump all the users or computers to look into their details.
Frequently Asked Questions
Here are the answers to the most frequently asked questions .
What are the local requirements to run PingCastle?
PingCastle requires the dotnet framework 2 for the report generation. The reporting program requires the dotnet framework 3 to use the OpenXML library. Consequently Operating Systems starting from Windows 2000 are supported.
What are the domain requirements to run PingCastle?
PingCastle requires a network connectivity to the domain such as LDAP (tcp/389), ADWS (tcp/9389), SMB (tcp/445) and authorization to connect on the domain which is granted by default to local domain accounts or accounts from trusted domains.
Is PingCastle GDPR Compliant?
PingCastle respect the principles defined by the EU and try to minimize the amount of data collected. Being decentralized allows you to be the data controller and processor to meet a stricter policy.
Where can I find the list of rules used during an assesment?
PingCastleReporting can produce an Excel file containing all the rules. PingCastle can produce an HTML report containing the same data. As part of our continuous integration process, the most recent list is available here.
Are you collecting any information?
PingCastle does not collect any other information that the one written in the report. No internet connectivity is required except if you want to verify the signature of the binaries.
Does PingCastle work in disconnected network?
Yes, PingCastle does not requires an internet connection. Furthermore the machine readable report can be encrypted using a RSA key which is suitable for email transfer.
How do you handle data privacy?
The only data collected related to the GDPR regulation is the administrator account name, account creation time and last login time. This data is contained in the human readable report and the auditor is accountable for its use. The machine readable report is expunged from all the account information by default and is not relevant to this regulation.
How can I protect the data contained in the report?
The report may contains data that is, based on our security policy, restricted. This can be a problem when you have to transfer this data over the network. To limit that risk, PingCastle can work on report encrypted with a RSA key: the report can be stored encrypted or transmitted safely while only the instance having access to the private key can process it.