Health check
This is the default report produced by PingCastle.It does quickly collect the most important information of the Active Directory to establish an overview on it. Based on a model and rules, it evalutes the score of the sub-processes of the Active Directory. Then based on this evaluation, it report the risk evaluation of it.
Prerequisites
AD connectivity
Access to the Active Directory via a local account or an account from a trusted domain
No local requirements
PingCastle requires only the dotnet framework version 2 available starting from Windows 2000
No domain requirements
Any users can query the objects stored in the domain or the GPO objects.
Build it
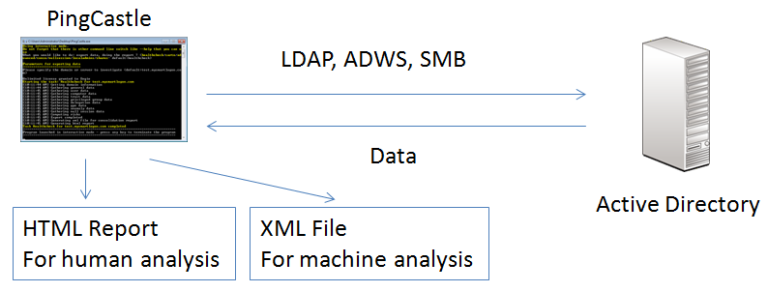
The report can be generated in the interactive mode by choosing “healthcheck” or just by pressing Enter. Indeed it is the default analysis mode.
It can be run using the command:
PingCastle.exe --healthcheck --server mydomain.com
Description
The report is divided in 4 parts. The parts are described below.
The most recent list of rules used by PingCastle is available here.
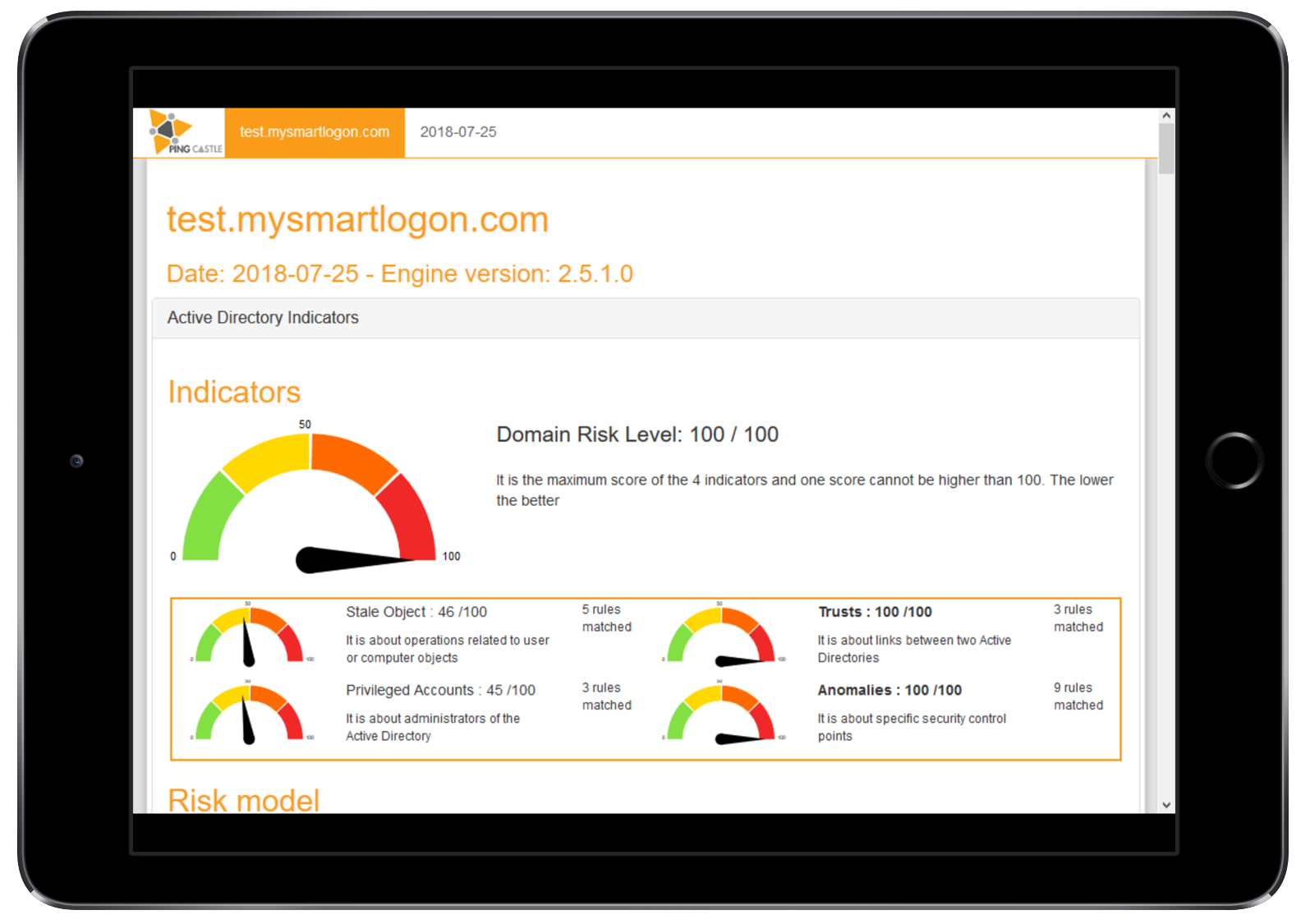
Scores
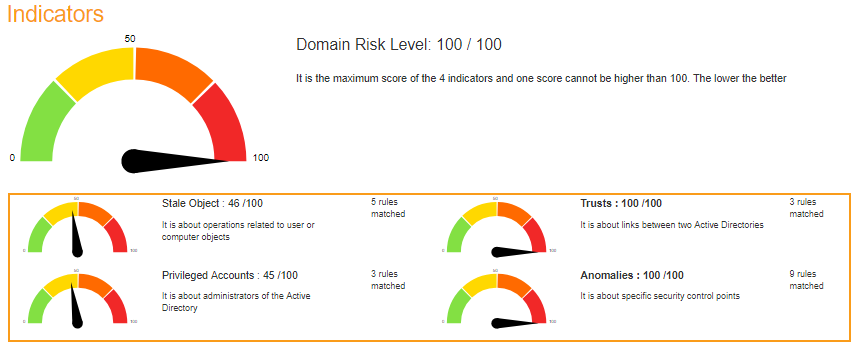
The Score is computed by the maximum of the 4 sub scores:
-
Privileged accounts
It is about administrators. -
Trusts
It is about the links between Active Directories (reminder: one AD can compromise one other via trusts). -
Stale objects
Stale objects represent everything about the AD objects and their life cycle: computer and user creation, delegation. -
Security anomalies
Everything that doesn’t fit into the previous categories. For example the security check processes.
Rules
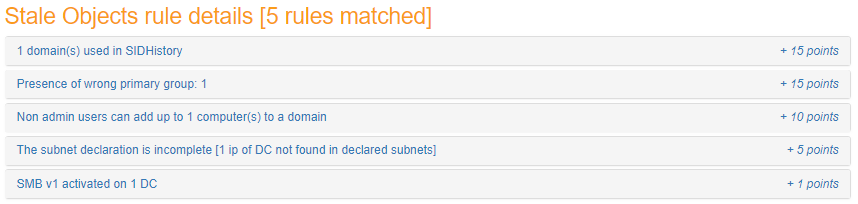
The details of the rules triggered is shown with some indication and the number of points calculated (the total cannot be above 100).
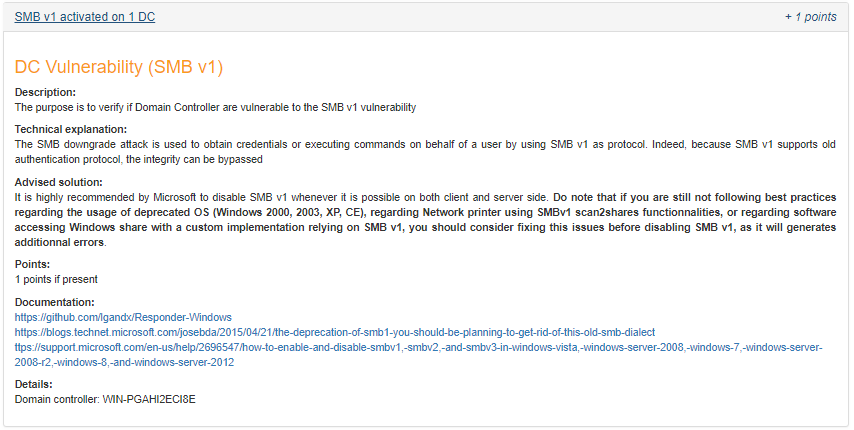
When the button “solve it” is clicked, a short explanation of the rule is shown with some indication on how to solve the situation.
General information
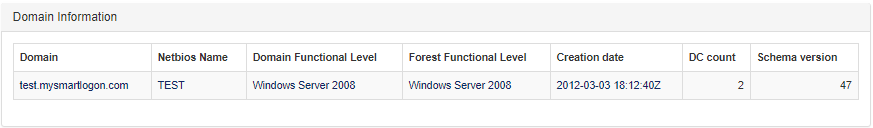
The report contains the information about PingCastle (version, generation date, …) and about the domain checked.
Details
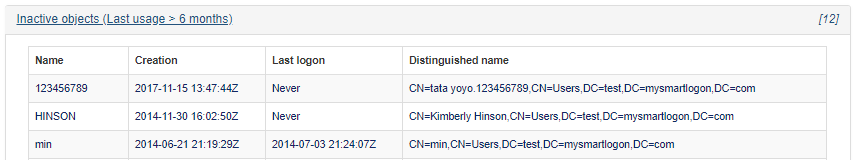
The Detail zone shows general information about users, computers, trusts, group policies, …
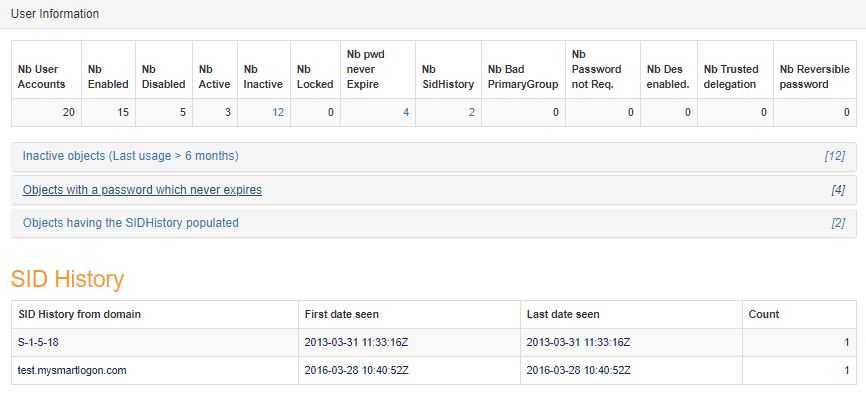
Some information can be seen in detail by clicking on the associated link. It contains data to help identify the underlying objects.